Cyberthreats Are Evolving—Are You?
Because of 9/11, the US Navy recognized a new kind of threat that existing data availability strategies were not architected to meet. And so, between 2002 and 2004 Vervint was involved in a massive project with the US Navy to set up advanced data replication for the Naval Air Systems Command (NAVAIR) to protect data related to Marine Corps and Navy aviation assets.
Today, we have a new kind of malevolent actor: the ransomware attack. Vervint has supported many of our customers in preventing these cyberattacks and in the remediation following an event.

Immediate Steps for Ransomware Protection, Mitigation and Prevention
However, just as the threat of having a secure facility in the US directly attacked led to changes by NAVAIR in the early 2000s, new threats mean that organizations need a new recovery strategy. What does that look like? Immutable storage.
Immutable storage needs to be added to the storage and server portfolio of every enterprise IT organization. This is a new imperative.
Backup can no longer be approached with a “set it and forget it” mentality. Your fifteen-year-old backup solution using virtual tape, physical tape (yes, we still have customers doing that) and spinning disks will not protect you against someone with criminal intent.
Immutable Storage Is Now a Necessity
Immutable storage is critical to new backup solutions. With immutable storage, your data cannot be changed or deleted. Even if the array or the appliance is put through a factory reset state, the data remains unchanged until the defined threshold period has been met. Immutable storage allows for object recovery to the last known good state, which is crucial if you have had latent ransomware in your systems for 60 days, 120 days or even longer.
However, immutable storage is not a magical backup and recovery solution that can meet all needs. Recovery technologies need to address three key purposes in addition to cyberthreats:
1. Long-Term Archive
Medical, legal and compliance data often needs to be retained for decades, if not indefinitely. For example, maternal ultrasound tests in high-risk pregnancies must be retained for over 20 years in many states. Architectural support documents should be retained for at least the same duration as the legal statute of limitations on filing suit, which is 10 years in many jurisdictions. And most businesses keep tax records, contracts, permits and other important financial records permanently, regardless of legal requirements.
2. Disaster Recovery
After natural or man-made disasters such as earthquakes, fires, etc., your business will need large-scale data recovery for major sites or individual data centers. Depending on your industry and business size, transactions, medical records and other mission-critical data and applications need to be replicated to the last known good state. And they need to be hosted at high-performance service levels so that recovery can occur as quickly as possible.
3. User Error
Any good recovery solution should include simple recovery to the last good copy of data under user control. This not only avoids calls to the help desk, but also reduces downtime across teams.
Metrics for Backup and Recovery Success
We have historically used the metrics of recovery point objective (RPO) and recovery time objective (RTO) to describe how much data we are willing to lose and how long we are willing to wait to get it back.
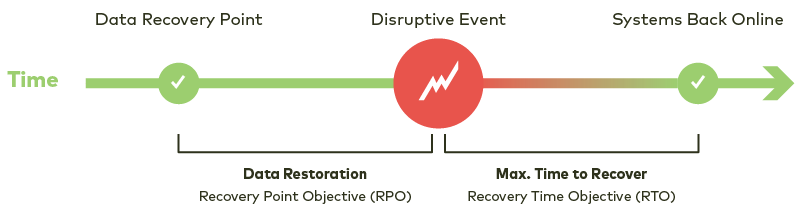
We use the metric of retention period to describe how long we want to save and retain access to a copy of this data.
For immutable storage protecting against cyberthreats, we add a fourth metric: recovery capacity objective (RCapO). We checked the Online Storage Networking Industry Association Dictionary related to data recovery to see if this term has been defined formally, but it has not. Recovery capacity objective is a term that has floated around the industry informally, and it refers to a defined percentage of your ability to run recovered application workloads compared to production.
In a cyberthreat recovery, one of the most important questions we have worked through in developing solutions for clients is this: “how will the data in the immutable storage be used after the launch of the ransomware attack to bring the organization online?” The recommended architecture will be highly dependent on this metric, which legitimately varies across our enterprise clients based on their size, industry, and other factors.
Of course, other components play into a data protection strategy against cyberthreats: airgaps, appliances versus traditional arrays, proprietary file systems and operating systems, etc. These nuances vary from vendor to vendor and are better discussed on a whiteboard than in an article like this.
Vervint: Helping You Protect, Recover and Retain Your Critical Data
Your organization’s backup and recovery portfolio is complicated. It’s time for modern recovery solutions that can effectively counter modern cyberthreats. Want to get started? Schedule some time with an expert or send us a message. We look forward to speaking with you!


